Cyber attacks are evolving as the technology is improving. Hence, it is essential to protect the data and devices connected to your network with cybersecurity. Without a well-defined cybersecurity program, it is hard for organizations to withstand any types of cyber attacks. This would eventually make your organization an inescapable target for the cyber criminals.
In this article, we, at LEAP Managed IT, are going to share all the necessary information on cybersecurity, different types of cyber attacks and ways to prevent them. Indianapolis cybersecurity experts at LEAP Managed IT are here to help in framing a suitable cybersecurity plan for your organization.
What is CyberSecurity?
Cybersecurity is a practice adopted by organizations and individuals to protect their data and computerized system from unauthorized access. It helps in providing a good security posture that would help in preventing your data from malicious attacks. It is difficult for an organization to survive without the implementation of a cybersecurity plan.
Importance of CyberSecurity
Cybersecurity is on the rise due to evolving cyber threats. It is a proven fact that whether it’s an individual/business, it can no longer entirely rely on security solutions like antivirus software, and firewalls as cybercriminals are getting smarter. Cyber threats can affect any level of organization, hence, it is essential to cover cybersecurity in every aspect. Data leaks could be identity theft, sensitive information, payment information and more. Hence, implementing a powerful cybersecurity plan must be made mandatory to keep your business secure.
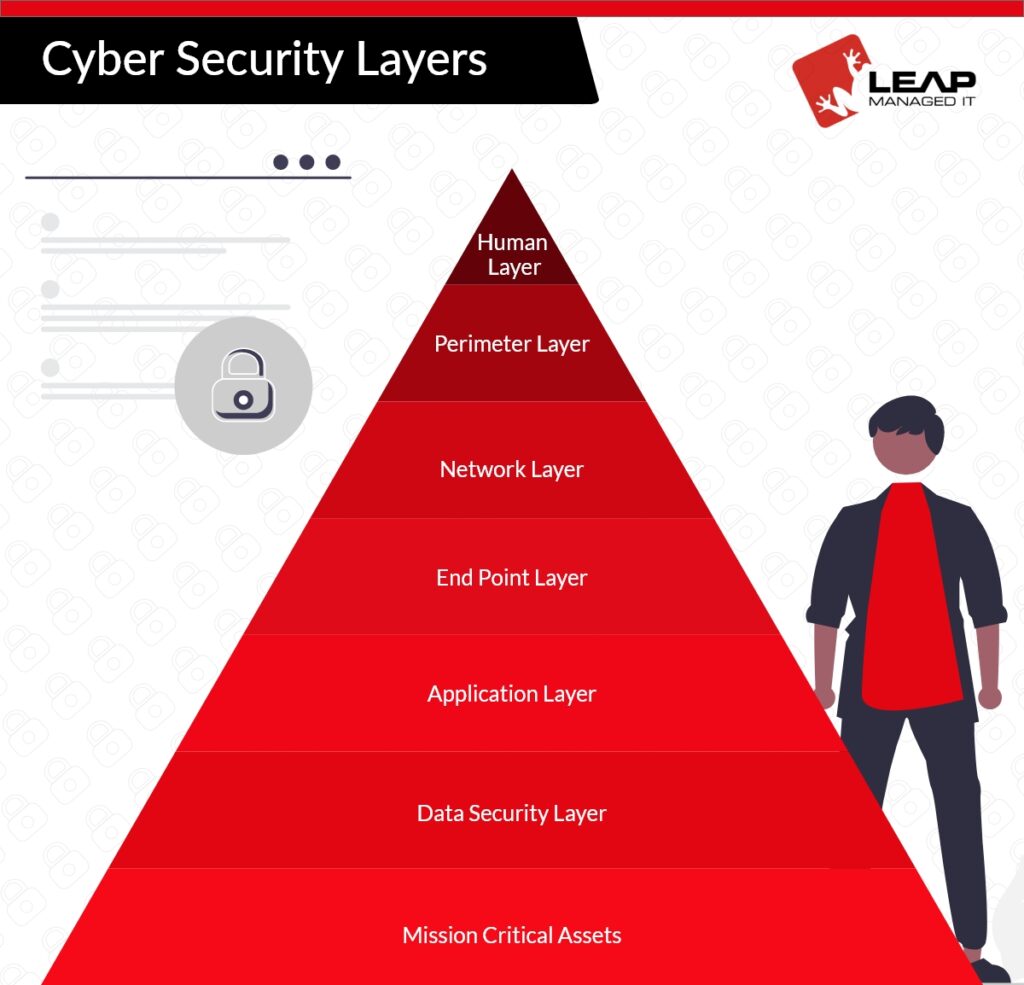
CyberSecurity Layers
The International Standard Organization, by realizing the needs for standardization in computer networks, developed the OSI model. The OSI model has 7 layers of cybersecurity that represents the interconnection between various layers on a network.
Mission Critical Assets
This layer would contain the operating system, electronic recorder, software tools, financial records and cloud infrastructure. It is anything that your business would find it difficult to survive without its existence.
Data Security Layer
Data is the ultimate target when it comes to cyber crime. This is the most crucial layer as it contains data that is dependent on your business. It can include information like customer details, payment information, social security numbers, and any other sensitive information. Losing this data disturbs the trust your customers have in your business. It is necessary to keep things safe at this level using regular backups, implementing 2FA, disk encryption and more such secure processes.
Application Layer
This layer is all about the applications and software that are being used by your business. Ensure that the software and applications are always updated to keep things moving securely, and this also helps in fixing the security problems. In addition to this, there are applications with firewalls integrated, usage of sandboxes for browser based applications and also the implementation of restricted policies for software which help in preventing unauthorized access from penetrating your business.
End Point Layer
Any device that is connected to your network is referred to as an endpoint, and there are many. It’s critical to have an effective policy in place to manage and monitor these endpoint devices. At this level, encryption is crucial, to make sure that the devices themselves are operating in secure environments. Another crucial component of endpoint security is mobile device management (MDM). It gives you remote access to devices while also limiting access to specific devices on your network. To stop further damage, this feature can be used to lock down mobile devices and erase all of their data.
Network Layer
This layer is all about who and what devices are connected to your network. It also includes what can be accessed when inside your system. To protect this layer, ensure to provide access to employees and devices only that requires it. This would help in limiting the damage caused by human error and will also reduce the impact on the compromised devices.
Perimeter Layer
This is the outer layer of the network and is all about considering everything that is connected and has access to your data. Get to know how this layer looks and ensure to secure everything that is connected – data and devices and make it a secure zone for an additional layer of protection.
Human Layer
Human error seems to be the driving force behind the majority of cyber attacks that are evolving. Researchers have found that nearly 88% of data breaches have occurred due to employee mistakes. It is the weakest layer, and to secure it, user education is essential. Educating your employees and users on the benefits of well-structured cybersecurity practices can bring in drastic changes to your business.
Different types of CyberSecurity Threats
Some of the most common cyber threats are,
Malware Attacks
One of the most serious cyber threats. Hackers create malware, or malicious software, to encrypt data, steal or delete it, take over a computer’s essential operations, and even monitor user activity. This gets distributed through physical drives, USB external drives and even through internet downloads.
Phishing Attacks
The most frequent and widespread cyberattacks. Here, hackers enter using a fake identity to trick users to give them sensitive and private information, visiting malware pages and downloading malware. Signs of phishing attacks are: odd sense of messaging, unusual request for sensitive information.
Weak Passwords
Another major risk to any business is the use of passwords that are weak and simple to guess. Small and medium-sized businesses typically have multiple accounts for different cloud-based services. Using the same password across several accounts is comparable to making the data vulnerable to hacking. Having weak login credentials would make the cyber criminals penetrate and access data easily.
Insider Threats
This threat occurs due to action caused by members within the organization. Here, these members get access to critical data which can cause harmful effects through ignorance and carelessness. Employees having access to multiple accounts may put the organization at risk, causing financial damage.
Ransomware
Every year, thousands of businesses are victims of ransomware, a profitable type of cyberattack. In this case, the hacker encrypts business files or data and demands a ransom. This attack spreads through phishing emails or by visiting websites with malware.
Social Engineering
Here, the leakage of confidential information is, due to human error. This is the biggest security threat today. Through this attack, hackers manipulate users into breaking standard security procedures. This attack is mostly carried out in the form of email phishing.
Accidental Sharing
Accidental sharing is always a threat, and it happens whenever information sharing takes place accidentally. It’s not due to malware or hackers. This occurs due to human error. Hence, this can happen through any medium. Any data shared accidentally when misused would create a negative impact on your business.
Tips to Prevent Cyber Attacks
- Create strong passwords
- Ensure to use a proper password management would help in handling passwords efficiently
- Implement two-factor or multifactor authentication
- Use spam filters and beware of email attachments
- Beware of suspicious links
- Keep your software updated
- Make use of secure Wi-Fi connections
- Keep your software and applications always updated
- Train your employees on social engineering attacker
- Create cybersecurity awareness through user education
- Secure mobile devices
- Have a backup and disaster plan
- Do not share passwords, access codes, or any digital data with someone you never know
- Never share confidential data through emails
Get Secured Today
Every day, businesses of all sizes are exposed to a variety of threats. The best thing a company can do to defend against threats is to put in place thorough security measures and to educate its employees about cybersecurity. This would guarantee that everyone connected to your company works with a consciousness about security threats and respective defense strategies.
To know more about cybersecurity from our experts in Leap, click here.
Are you looking for expert guidance on cybersecurity threats and their prevention methods? Visit our website, Leap Managed IT. We can help you with the best solutions by understanding your requirements. In the same way, we handle Managed I.T, phone, Process Automation, and more. Like us on Facebook and get more Ridiculously Helpful tips for your business.
To learn more about LEAP Managed IT, check out this video.